The full guide to integrating Zuora in your website
Giants like Shopify and Amazon have set the bar impossibly high. Today's customers demand lightning-fast performance, seamless mobile experiences, and bulletproof security—all while expecting instant gratification. For subscription businesses, the complexity multiplies. Beyond standard ecommerce challenges, you're juggling recurring billing, complex pricing models, and platform integrations with Zuora. This guide walks you through building a subscription ecommerce site from scratch, tackling everything from product pages to order orchestration, with practical solutions for the unique challenges of subscription commerce.

Introduction
Building an ecommerce website in 2023 isn’t a novel thing, but it doesn’t mean it is easy. Customers have high expectations, expecting fast loading times, mobile-friendly content, localised content, secure transactions and more. Providers such as Shopify and Amazon have transformed the ecommerce market and reset customer’s expectations to sky high-level. It would be nice if you could hook up Zuora and Shopify and be done with, but unfortunately it isn’t that simple. Here’s what you’ll need to think about:
- Lightning-Fast Performance: In a world where every second counts, speed is king. A fast-loading website isn't just a nicety; it's a necessity. Shoppers expect pages to load in the blink of an eye. Delay can mean the difference between a sale and a lost customer.
- Mobile-Friendliness: With the majority of internet users accessing websites via smartphones even in B2B commerce, your ecommerce platform must be mobile-friendly. This means not just being accessible, but also offering a seamless, intuitive shopping experience on smaller screens.
- User-Friendly Design: Clarity and ease of navigation are crucial. A well-designed website guides customers effortlessly from browsing to buying, with clear categories, simple search functions, and an uncomplicated checkout process.
- Personalised Experience: Consumers appreciate a shopping experience tailored to their preferences. Utilising data analytics to personalise product recommendations can significantly enhance user engagement and sales.
- Robust Security: In an era where data breaches are all too common, robust security measures are non-negotiable. Customers need to trust that their personal and payment information is safe.
- Local Currency, Language, and Locale: Catering to a global audience means accommodating local preferences. This includes displaying prices in local currency, translating content into the local language, and adjusting for cultural nuances and local market trends.
In this guide, we'll assume you are building a website from scratch. If you aren't, feel free to skip some sections such as building a website. Enjoy!
Building a website
To fulfil those expectations, you will need to get building and coding. You will need to set up a DevOps infrastructure, front and back-end frameworks, and release processes. The key areas will be:
- Domain and Hosting: Choose a relevant domain name and a hosting service suitable for your website's scale and traffic.
- Front-End Development: Use HTML, CSS, JavaScript, and frameworks like React or Angular for designing the user interface.
- Back-End Development: Employ languages like Python or Node.js and databases (SQL/NoSQL) for server-side processing and data management.
- DevOps and Deployment: Implement version control with Git and automate deployment using CI/CD tools like Jenkins or cloud services like AWS.
- Testing: Conduct unit, integration, functional, and performance testing to ensure robustness and reliability.
- Security: Secure data transmission with SSL/TLS, regularly update software, and use security tools like firewalls and anti-malware.
- SEO and Analytics: Optimise for search engines and use tools like Google Analytics for insights into traffic and user behavio
Now the nice thing is none of this is specific to Zuora, so you will find plenty of developers happy and willing to help. The basics for a subscription ecommerce website are similar to a regular website, but we’ll tackle all the particularities and specificities of subscriptions commerce in the next sections, and in particular Zuora commerce.
How Limio can help
Limio creates a high-performance, mobile-friendly, secure commerce website for you, so you don’t need to think about hosting, framework, infrastructure, testing, security, SEO and analytics. It all comes off-the-shelf, which you can then host on your own custom domain and plug-in your analytics infrastructure.
Create your product and pricing pages
Ok so you have the barebone of a website, now it’s time to create your Zuora Commerce website! First thing first, your customers need to browse the catalog. For subscriptions, it can be fairly simple (e.g. Spotify Free, Spotify Premium, Spotify Family) as opposed to sprawling ecommerce catalog. It can however be more complex if you have many products and add-ons. So let’s break down what you need to think about. We’ll merge in product and pricing pages, as a lot of subscription products will present all the information in one place, but you could also separate them.
Product & Pricing Page:
- Content or Product Descriptions: For digital subscriptions, describe the type of content (e.g., courses, e-books, software); for physical products, detail what items are included in each delivery.
- Subscription Options: Detail the different types of subscriptions available, such as monthly, quarterly, or annual plans, and any variations in the frequency of deliveries or access.
- Trial and Demo Information: Provide details on any free trial periods or demo versions, explaining what is included and how to sign up.
- Promotional Discounts: Highlight any introductory offers or discounts for new subscribers, and explain how and when these apply.
- Plan Comparison: If offering multiple tiers, provide a side-by-side comparison of features, benefits, and prices for each tier.
- Bundling Options: If bundles are available (e.g., combining different products or services), clearly outline what each bundle includes.
- Customization Options: If subscribers can customize their subscription, provide clear instructions and options for doing so.
- User Reviews and Testimonials: Share feedback from current subscribers to build trust and provide insight into the subscription experience.
- FAQ Section: Cover common questions about subscription terms, cancellation policy, pausing subscriptions, and any other relevant details.
- Cancellation and Refund Policy: Detail the process for cancelling a subscription and any refund policies that apply. This can be mandatory in some regions or for certain products.
Again, not much that is specific to Zuora Commerce, though you will need to pull the price from somewhere. Do you hardcode them on your website, store them on a local database, or do you pull them dynamically from Zuora? Let’s consider the options:
- Hardcoding Prices on the Website:some text
- Pro: Simple setup with direct control over price changes.
- Con: Time-consuming updates via a developer and poor scalability for large or frequently changing catalogs.
- Storing Prices in a Local Database:some text
- Pro: Dynamic pricing with centralised data management and integration potential, faster load times.
- Con: Requires more infrastructure maintenance and regular synchronisation for accuracy.
- Pulling Prices Dynamically from Zuora Catalog:some text
- Pro: Real-time pricing accuracy and automated updates tailored to customer behaviour.
- Con: Relies on Zuora's system reliability and can impact website performance if not optimised.
The right option for you will depend on the use case. Simple pricing with little promotional activity? Hardcoding might be fine for those simple use cases or to start with. More pricing with lots of promotional activity and where load time is critical? Storing prices in a local database will make more sense. Complex pricing such as consumption-based price? Pulling prices from Zuora will guarantee the best accuracy, but the experience might be slow. A good workaround can be to show prices such as ‘From $99 a month’ or ‘Starting at $9/user/month’ and performing calculations in a cart in the cart or checkout. Don’t forget you’ll also need to pull the name of the product and pricing from somewhere, and this could change with time (Digital - 50% off).
How Limio helps accelerate pricing pages
Limio has many off-the-shelf components that help to create product & pricing pages rapidly, from pricing displays, to FAQ, to banner displays. Our components can display pricing stored in Limio for speed or can query Zuora for more complex pricing for example for B2B consumption-based pricing. You can also leverage the Limio SDK to create any visual experience you want.
.png)
Creating a cart/basket
In subscription commerce, having a shopping cart is often deemed optional because the purchasing process typically involves selecting a subscription plan rather than adding multiple individual items to a cart. However, even if not prominently displayed, maintaining a "hidden" cart system can offer several benefits:In essence, while not always front and centre in subscription commerce, a cart system, even if hidden, offers valuable tools for customer engagement and operational flexibility. So if you want to create a cart, how do you do it? Zuora doesn’t include a cart concept in its application or APIs, so you’re on your own here and will need to build the logic as part of your website. What are the key components of a cart?
- Product Details: Name, description, and image of the product or subscription plan, providing clear and informative details about what is being purchased.
- Quantity (optional): For e-commerce, the number of each item; in subscription commerce, it might indicate the number of subscription units or duration.
- Pricing: Displays the price for each product or subscription plan, updated in real-time for changes in quantity or duration. This may require API calls to Zuora if quantities are updated for example. This can be quite complex if you have consumption-based pricing and promotions applied.
- Promo Codes: A field for entering discount codes, with the cart recalculating the total price upon applying a valid code. Promo codes aren’t natively handled by Zuora, you will need to build your own solution or consider add-ons.
- Total Calculation: A dynamic total that updates with changes in the cart, including itemised costs like taxes (if possible) and discounts. Again, this may require API calls to Zuora to retrieve the correct calculation.
- Update Mechanism: Functionality to change quantities or remove items, with immediate recalculation of the total cost.
- Checkout Button: A clear and prominent button leading customers to the next step in the purchasing process.
There's a couple of other complexity to handle:
- Analytics: If you build a data-layer, you'll need to make sure to track the add_to_cart and remove_from_cart events with the relevant product information.
- Multi-domains: If you have multiple subdomains but want to persist the cart across them, you'll need to think about a cookie or server-side solution. If it's a cookie, you'll need to make sure to clear it after the purchase is done.
- Abandoned Checkout Tracking: A hidden cart allows you to track when potential customers add subscriptions to their cart but don't complete the purchase. This data is valuable for understanding customer behaviour and for retargeting efforts, such as sending reminder emails to encourage completion of the purchase.
- Upselling and Cross-Selling: A cart system can facilitate upselling and cross-selling by suggesting additional or complementary subscriptions before checkout. This can enhance customer experience and increase revenue.
- Flexibility for Customers: Even in subscription models, customers might appreciate the flexibility to manage multiple subscriptions (like adding, modifying, or bundling different plans) before finalising their purchase. A cart system makes this process more intuitive.
How Limio manages baskets & carts
Limio facilitates Zuora Commerce, so Limio always has a cart, whether visible to the user or not. This allows marketers to create abandoned cart campaigns, but also gives the flexibility to cross-sell and upsell offers and add-ons down the line. If the cart is visible, Limio has standard components that can be embedded on any page on the website or have its own dedicated page (or both!). The cart can be also custom-made via the Limio SDK. Cart information is stored in a cookie that can be shared with other areas of the website.

Hooking up authentication and registration
In the retail world, no one likes to be forced to create an account before purchasing a product. It’s well-known that it hurts the conversion funnel But in the subscription world, this is often a must-have. Subscriptions are complex products that require self-service - without registration and authentication, how will customers manage their subscriptions? So while it’s possible to skip authentication, it’s not best practice.
Not only will it make the customer experience more convoluted, but if you have an unauthenticated checkout, it makes provisioning an order much more complex. You will need to think about how you link the order to the customer’s identity. Post-purchase, there will need to be mechanisms to require the subscriber to create their account, but none are error-proof. Do registration on the order complete? The customer can close the tab. Do it via email? It can end up in spam or ignored. And there are complex edge cases, for example what if the customer makes a mistake in their email, how do you resolve those issues and assign the subscription to the correct identity?
Spare yourself some pain and plan to build and maintain an authentication mechanism as part of your ecommerce. If you already have an authentication mechanism, which most media or SaaS customers will already have, then you should re-use that. If you don’t have currently like most retail companies, then you’ve got two options:
- Build Your Own Authentication System:some text
- Pros: Tailor-made to fit specific requirements, offering full control over the authentication process and data. It can be more flexible in terms of integrating with existing systems and workflows.
- Cons: Time-consuming and expert resource-intensive, requiring significant development expertise. There's also the ongoing responsibility of maintaining security, updates, and compliance with data protection laws. It often will lack critical components such as OAuth, SAML, and OpenID.
- Buy/Use a Third-Party Authentication Provider (Auth0, Okta, AWS Cognito, Microsoft Azure, Salesforce Identity):some text
- Pros: Quick to implement, often just requiring integration into your system. These providers usually come with robust security measures, regular updates, and compliance with various data protection regulations. It also supports import frameworks such as OAuth, SAML and OpenID.
- Cons: Less flexibility in terms of customization. You're also reliant on a third party for critical security aspects and need to adapt to their system limitations and pricing models.
You will need to develop the UI for the authentication and registration. Most third-party identity platforms will have their own standards. If you plan on custom-building, developing the UI for registration and authentication should focus on simplicity, clarity, and security. Start by designing a clean and intuitive layout, with clearly labelled input fields for essential information like username, email, and password. You’ll need to incorporate visible validation messages to guide users through the process, and ensure that error messages are helpful without compromising security (don’t give away too much!). For a seamless user experience, integrate options for social media logins and remember to design for mobile responsiveness. Lastly, prioritise security features like two-factor authentication that is appropriate to your audience.
Last but not least, how do you link authentication to your overall customer identifier in Zuora and Salesforce (if they already exist). If you are john@smith.com, how does that relate to Zuora Account A-00001 and Salesforce Account ID 100AEXFF ? For example, to connect Zuora to Salesforce, Zuora requires a CRM ID at the time of creation, so that Zuora Z360 can show the relevant data in Salesforce. This is often work that needs to be carried within the authentication layer. Else you would need to query the external systems when creating the order, degrading the customer experience by increasing the order processing time due to the additional API calls involved. The best practice is to pass the relevant identifier to the identity provider, store them in the JWT token, and then use the information as part of the order provisioning.
How Limio manage identity
Authentication is one of the most difficult points of integrating your website with Zuora. Limio has spent years of development to make it seamless. For example, Limio can support both un-authenticated and authenticated purchases, and those can be for different use cases. For example, a gift or reseller purchase could be unauthenticated and all other owned-subscriptions purchases can be authenticated.
For authenticated purchases, Limio will federate identity with your identity provider via OAuth/OpenId, whether custom-built or third-party authentication provider like Zephr, Microsoft Azure, AWS Cognito, or Okta. The user will seamlessly go to your registration or authentication page, and if already logged-in, will seamlessly land on the checkout. Limio can also read a JWT token to pull the relevant identifiers such as Salesforce Account, so that this information can be distributed to various systems including Zuora, as well as segment information to create personalised experience.
Don’t want to do that? Limio is able to orchestrate the order to first create information in Salesforce and pass them to the necessary fields in Zuora. And the beauty of all this is that all this can be achieved with zero code, just point & click within the Limio platform.
Building your checkout, including payments, tax, and address validation
The checkout is likely the largest beast to tackle in subscription commerce, even more complex than authentication. Offering a checkout that can cater to all the different subscription pricing, the complexity of certain baskets, the regulatory requirements around cancellation and price displays, and the ability to purchase, renew, upgrade throughout the subscription lifecycle is complex enough. But layer on integration for payments, tax, addresses, and the requirement for security and speed, as well as marketer’s desire to control the look & feel and experiment with different checkouts and it becomes a nightmare. We haven’t even touched how to do it specifically with Zuora.
Let’s breakdown the key components of a checkout:
- Flexible Pricing Structure Integration: The checkout system must handle various subscription pricing models (like tiered, volume-based, or per-user pricing) and support different billing frequencies (monthly, annually). It should also accommodate promotional pricing, discounts, and trial periods.
- Complex Basket Handling: The ability to manage multiple subscription products in a single transaction, including bundling different products or services and handling add-ons or upsells effectively.
- Regulatory Compliance: Ensuring the checkout process complies with global and local regulations regarding cancellation policies, price transparency, and consumer rights. This includes clear communication of terms of service, privacy policies, and return/refund policies.
- Payment Gateway Integration: Securely integrating with multiple payment gateways to offer a range of payment options (credit/debit cards, digital wallets, bank transfers). This includes express payment methods such as Apple Pay and PayPal.
- Tax Calculation and Compliance: Automatically calculating taxes based on the product, customer location, and local tax laws, including handling of VAT, GST, and other applicable taxes for different regions.
- Address and Delivery Management: For physical subscription products, efficiently managing shipping addresses, delivery options, and costs. This includes integrating with address prefill and validation services to streamline the checkout process, ensuring accuracy and speed in address entry. For digital subscriptions, ensuring the user's location aligns with service availability and compliance requirements.
- Security and Data Protection: Implementing robust security measures to protect customer data and payment information, including encryption, secure socket layer (SSL) certification, and compliance with standards like PCI DSS.
- UI/UX Design Flexibility: Allowing marketers and designers to control the look and feel of the checkout process, ensuring it aligns with brand identity and provides an intuitive user experience.
- A/B Testing and Optimization: Enabling the testing of different checkout flows, layouts, and elements to optimise conversion rates and improve the customer experience.
- Analytics and Reporting: Providing tools to analyse checkout performance, track abandonment rates, and gather customer feedback for continuous improvement.
To go further, you may need to think about:
- Multinational Checkout Support: Equip the checkout to handle multiple currencies and price zones, enabling customers to see prices and transact in their local currency. Additionally, offer multilingual support for the checkout interface.
- Different Checkouts: Support varied input requirements, such as options for gift recipients or company purchases. This includes fields for entering gift recipient details, special instructions, or company-specific information like tax identification numbers.
- Promo Code Integration: Implement a robust system for promo code application within the checkout. This feature should allow customers to easily apply discount codes or special offers, with real-time updates to the pricing and total cost.
- Upsell and Cross-Sell Mechanisms: Integrate upsell and cross-sell opportunities strategically within the checkout flow. This can include suggesting related products, upgrades to subscription plans, or additional services that complement the customer’s current selection. Such recommendations should be relevant and enhance the overall value of the customer's purchase, potentially increasing the average order value and improving customer experience.
Lots to think about right? So let’s define the key components and focus on doing the basics:
- User Details: Integrating the user details with the authentication layer is essential. This integration helps in automatically pulling relevant details to form the basis of the Zuora Customer Accounts. It ensures that the user's profile,
- Payment Details: The integration of Zuora Hosted Payment Methods (HPM) is crucial for secure and efficient payment processing for credit cards and bank-based payment methods such as Direct Debit and ACH. Additionally, incorporating express payment methods like PayPal and Apple Pay can enhance the user experience by offering more convenience and speed in transactions. some text
- A word on pre-authorization: Implement a system for pre-authorizing payments during the checkout process. This can be achieved by creating a standalone payment method in Zuora, which initially holds the payment details without processing the charge. This method ensures the validity and availability of funds on the customer's payment card. Once the order is confirmed and finalised, the pre-authorized payment method is then attached to the customer's account, and the charge is processed. This approach enhances transaction security, improves customer experience by reducing payment failures, and ensures compliance with payment processing regulations.
- A word on non-supported gateway: A word on non-supported gateways: If you hear the term "non-supported gateway" from Zuora, brace yourself for a considerable amount of work. Zuora offers a Universal Payment Connector framework that enables the integration of any gateway. However, this setup is fairly complex and requires substantial technical expertise in API integration and customization. You'll need to understand the specific API calls and data structures of your chosen gateway and ensure they align with Zuora's payment processing workflows. Additionally, maintaining compliance with payment security standards and handling error scenarios becomes your responsibility. This path requires thorough planning, development resources, and continuous maintenance to ensure seamless payment processing.
- Address Details: Collecting accurate billing and delivery addresses is vital, especially considering the different address formats in various locales. Integrating with a prefill or validation service, such as Google Maps, streamlines this process by automatically suggesting addresses and validating their accuracy. These addresses then need to be correctly mapped to the BillTo and SoldTo fields in Zuora, ensuring that billing and delivery information is accurately reflected in the system.some text
- A word on billing address: Not every payment methods require you to collect a billing address in the checkout. For example, PayPal and Apple Pay will have a billing address available and it will be a better experience to reuse that (less fields for the customers to provide in the checkout). That said, you'll need to think about the consistency of your address data (if that matters to you), as you may attempt to collect less information for debit and credit card (for example just state + ZIP code, but not the first line of address or the city). For debit/credit card, you will need to discuss with your payment gateway what is the least amount of address data you can collect without increasing the fraud and chargeback exposure risk.
- Basket: Maintaining a clear and interactive view of the customer's basket is important. This includes not just listing the items selected for purchase but also allowing for easy modifications, such as adding or removing items, changing quantities, or applying promo codes. This dynamic basket view helps customers in making final decisions and ensures that they are aware of the total cost and details of their purchase. To do that, you may need to regularly query Zuora via Zuora Preview to reflect the price based on different input. some text
- A word on tax: In the US and Canada, tax can only be calculated once the address of the customer is known. This will require retrieving tax through a Zuora Preview once you have sufficient information. This can rapidly be complicated if you want to show clearly to the customer tax due while keeping the experience simple and showing full costs as upfront as possible.
- Submission: The final step involves triggering the order processing once the customer completes the checkout process. This involves sending all the collected data (user details, payment information, addresses, and basket contents) to Zuora for processing.
Et voilà, you’ve got a checkout that can handle a purchase and make the Order API call to Zuora to create a Zuora Customer, Zuora Subscription, Zuora Payment Method, Zuora Contacts, Zuora Invoice and Zuora Payments. But let’s not get ahead of yourself as that’s in the next section.
How Limio Modular Checkout lets you experiment
Limio aims to dramatically simplify creating a checkout that is incredibly flexible for marketers - letting them experiment with while integrating seamlessly with the necessary systems including Zuora.
Limio’s Modular Checkout allows users to flexibly drag & drop different components such as user, address and payment fields in different places and configure them via a no-code interface. Out-of-the-box integrations with authentication providers such as AWS Cognito, address prefill such as Loqate, and payment and tax via Zuora allow companies to plug & play rapidly with a functional, mobile-friendly, performant checkout.

Preventing fraud in your checkout
Let’s talk about a serious topic: fraud. If you have a checkout, it will attract fraudsters. Checkouts are highly sought after targets as the British Airways hack showed years ago (with a £183 million record fine). So you will need to implement security features such as rate limitations, ReCAPTCHA, and more.
Luckily, Zuora (and Limio) are PCI-compliant so it will reduce the amount of things to care about such as card tokenization and encryption of payment data. But here’s what you’ll still need to worry about:
- SSL/TLS Encryption: Implement Secure Socket Layer (SSL) or Transport Layer Security (TLS) to encrypt data transmitted between the user's browser and the website server.
- Fraud Detection Algorithms: Use algorithms to analyse transactions for suspicious patterns and prevent fraudulent activities.
- Secure Checkout URLs: Employ HTTPS for checkout pages to ensure encrypted communication.
- Data Encryption at Rest: Encrypt sensitive data stored on servers to protect it from unauthorised access.
- reCAPTCHA: Integrate reCAPTCHA to distinguish human users from bots and mitigate automated attacks.
- Rate Limiting: Implement rate limits on API endpoints and user actions to protect against excessive requests, reducing the risk of DDoS attacks.
- Cross-Origin Resource Sharing (CORS) Policies: Establish and enforce CORS policies to control which domains can access your website’s resources, mitigating cross-site scripting risks.
- Input Validation: Rigorously validate user inputs to prevent SQL injection and other injection attacks.
Fraudsters don’t sleep sadly and so you will need to continuously monitor your checkout and implement good practice with your company such as:
- Regular Security Audits and Penetration Testing: Regularly audit and test the security of your website to identify and rectify vulnerabilities.
- Limited Data Retention: Minimise and regularly purge unnecessary personal and payment data.
- Staff Training: Educate staff on data security practices and the importance of customer information protection.
How Limio keeps you safe
Limio is PCI-compliant so needless to say, Limio’s Modular Checkout is built-in with security in mind. From SSL/TLS, encryption, CORS policy, rate limiting features and constant monitoring by our team, you can rest easy that we’re keeping watch.
Creating order orchestration infrastructure across billing, payments, CRM and entitlements
Congratulations, you’ve got your first order! Now what needs to happen? Well as it turns out, an awful lot. Typically, you will need to do things in the following order:
- Salesforce: You might think this will come last, but actually Zuora requires a CRM Id to be passed at the time of order. As discussed previously, this can come from an authentication layer or might need to be created at the time of order.
- Zuora: Create a new subscription in Zuora via the Order API. The Order API will combine multiple actions such as creating a subscription, adding products, and setting up billing and payment details into a single API call. A couple of extra details:some text
- You will likely need to pass data to custom fields, which will have to be stored from somewhere such as hard-coded from the website.
- You will need to populate the CRM Id from Salesforce.
- Entitlement or Fulfilment: Once Zuora has been successfully provisioned, you will want to rapidly pass entitlement or fulfilment information to a third-party system (or to more custom fields in Zuora!).
One of the difficulties here is that those calls must be made sequentially. Zuora needs the CRM ID coming from Salesforce, and entitlement systems need to know the order has been successful and paid for before provisioning access.
You may also want to send webhooks to other systems that are necessary to be aware of the new order in your architecture, for example an email marketing system.
And what about if something fails or there is performance degradation? Well guess what, you might need to build something to track failures, be it a reporting dashboard or an application. This will allow you to operationally manage failures, for example due to payments and follow-up with customers or send abandon basket campaigns, and slowness, for example due to latency between applications. It’s worth knowing that if something fails in Zuora, Zuora does a full rollback so you will have nothing created if the payment fails for example due to a gateway error (but you may have some data in Salesforce given it was the initial step).
How Limio provisions orders
Limio includes a flexible order plugin that allows to mix out-of-the-box integrations with leading apps such as Zuora and Salesforce, and embed custom logic, for example for custom fields, and integrate with additional critical applications.
All orders are tracked via events that include comprehensive reporting on order failures, allow for order resubmission in certain scenarios, provide full logs on order steps executed, and breakdown every API call and the response times for each step giving you full visibility on speed and performance.
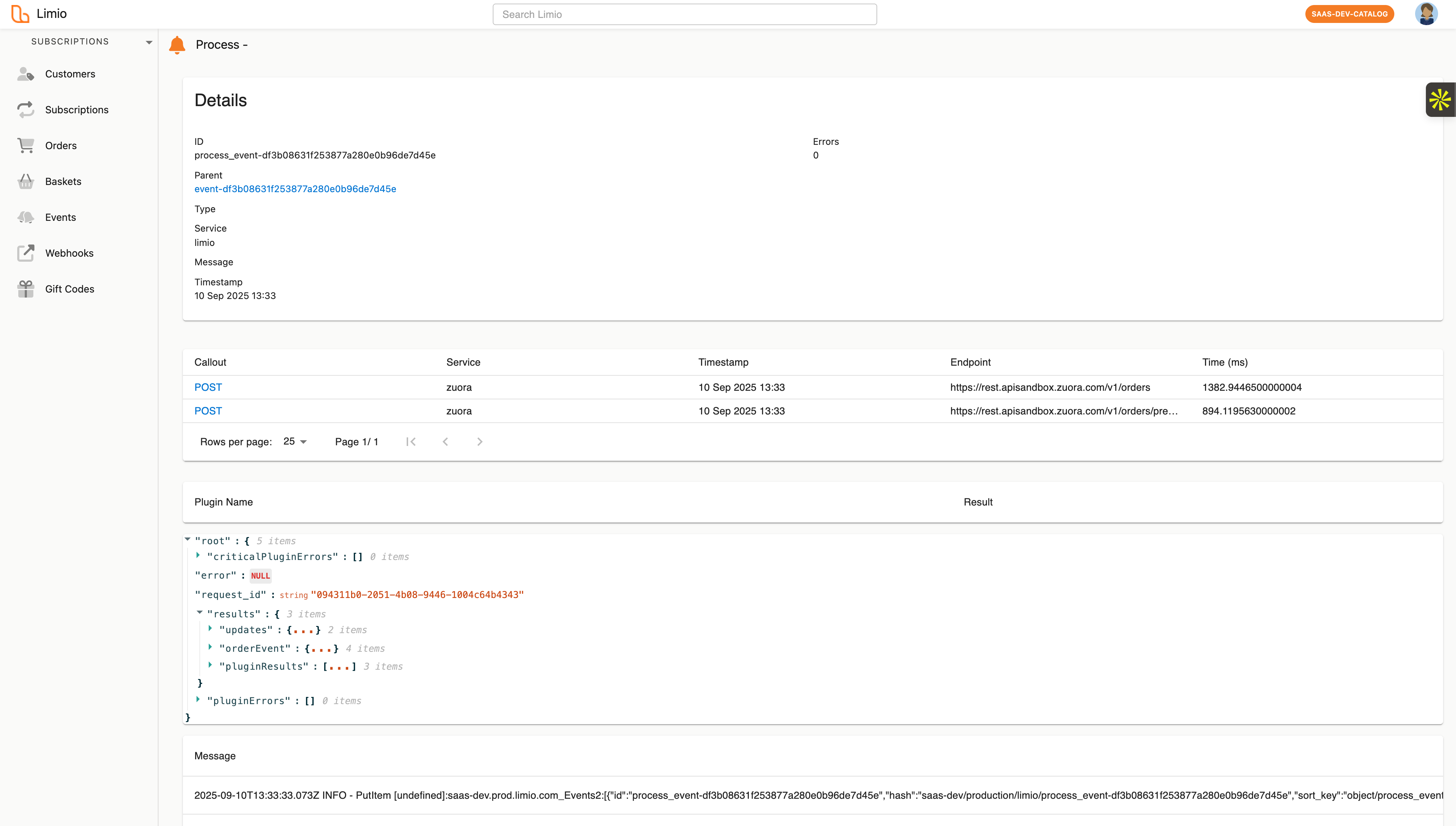
Create an order complete experience
Last but not least, you need an order complete page. They are typically three types of order complete page:
- Onboarding-focussed: Some order complete pages are more focussed on onboarding, fleshing out first steps such as downloading apps, learning about key features, or setting up more details on your accounts. This approach is more typical in SaaS or Media.
- Order-focussed: The order complete page might also recap the order, for example showing all the details captured including billing, delivery, payment details etc. This approach is more typical in Retail.
- Redirect: Some companies might decide to completely skip the order complete page and take the customer straight into the subscription experience. This will be more typical of consumer or B2B SaaS.
Regardless of the order complete page, there is one key challenge around order completion: how do you provision access and entitlements as soon as the order is completed? It is immensely frustrating to a customer to perform a purchase and then not get access to the product immediately. Yet, Access and Entitlement systems are often custom-built and therefore required to be integrated with the ecommerce systems. Integration means failures, race conditions, and performance degradation are all on the table. One safe way to make sure this doesn’t happen is for order to be synchronous, so the customer only gets to the order complete page once all systems have been provisioned.
An even better experience, especially for media companies, is being able to jump back into the trigger point of the purchase, for example an article where the paywall was triggered. This requires conserving the referrer through the whole conversion funnel and being able to redirect the customer, for example via a Call-To-Action, back to the article.
